Windows Defender Security Center Scam: Essential Tips to Shield Your Computer from Deceptive Pop-Ups
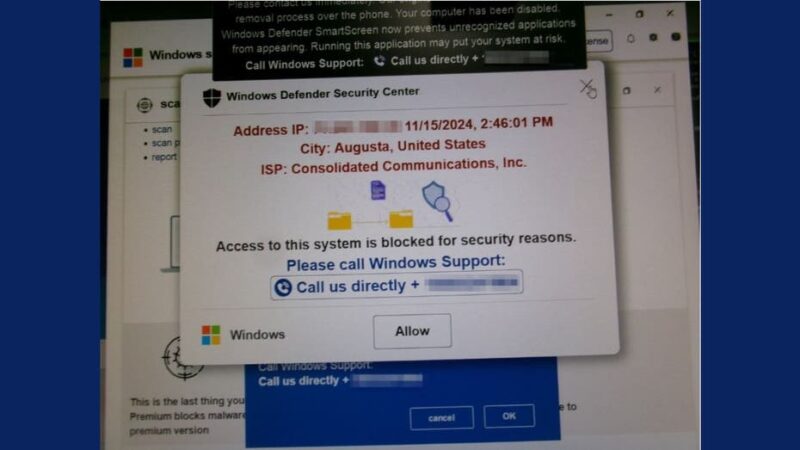
In an alarming email from Janet D., we learned about her recent encounter with a common online scam. Here’s her story:
“I was confronted with a pop-up that completely froze my computer and displayed a message stating, ‘Access to this system is blocked for security reasons’ from Windows Defender Security Center. To make matters worse, it came with an audio alert and a siren sound.”
### The Panic Response: A Cautionary Tale
In a state of panic, Janet took the bait and called the number presented on her screen. Though the scammer provided her with instructions to unfreeze her computer by pressing Ctrl + Shift + Esc, the situation quickly escalated. The scammer then urged her to download software from UltraViewer.net, a legitimate remote access tool frequently exploited by malicious actors. Here’s how to protect yourself from falling for similar scams.
### Understanding the Scammers’ Tactics
1. **Fake Alerts from Reputable Companies**: Janet’s experience underscores a prevalent tactic employed by scammers: fake alerts that impersonate official warnings from companies like Microsoft. It’s crucial to remember that legitimate organizations don’t send pop-ups with support numbers or direct users to download remote access software.
2. **Creating Urgency with Audio and Visual Cues**: Scammers often use alarming sounds and flashing visuals to evoke a sense of panic, compelling victims to act without rational thought.
3. **Requesting Remote Access Software Installation**: Malicious actors frequently ask victims to install remote access tools like UltraViewer, TeamViewer, or AnyDesk. While these tools can be legitimate for remote support, downloading them at the request of strangers is a significant red flag.
### Quick Actions to Take If You Encounter a Scam
If you encounter a suspicious pop-up, it’s crucial to remain calm and take decisive action:
– **Do Not Engage**: Avoid calling the provided number or following on-screen prompts. Instead, independently verify any suspicious messages or numbers.
– **Use Task Manager**: Press Ctrl + Alt + Del to open the Task Manager and close the offending browser or application.
### Assessing Your Security
Scammers thrive on urgency, but it’s essential to take a moment to assess your situation. If you find that you have installed UltraViewer or similar software, take these steps:
– **Uninstall Suspicious Software**: Remove any unauthorized applications immediately.
– **Change Your Passwords**: Update passwords for critical accounts, prioritizing email and banking logins. Consider using a password manager to generate and store complex passwords.
– **Enable Two-Factor Authentication**: This adds an extra layer of security to your accounts, making it harder for unauthorized users to gain access.
If you suspect your computer may still be compromised, consulting with a professional can ensure your system is secure. Additionally, consider reaching out to Microsoft Support for further guidance and to report the incident.
### The Role of Antivirus Software
Janet noted that her antivirus software failed to flag the scam. Many scammers rely on social engineering tactics rather than malware, allowing them to bypass traditional antivirus detection methods. Regularly running scans can still be beneficial in detecting hidden threats.
### What to Do After a Scam Encounter
If you find yourself victimized by a scam, follow these steps to safeguard your information:
– **Cease Communication**: Stop all contact with the scammer immediately. Do not respond to any further messages or calls.
– **Report the Scam**: Notify your local law enforcement or cybercrime unit about the incident, providing them with as much information as possible.
– **Notify Financial Institutions**: If you shared any financial details, contact your bank and credit card companies to inform them of the potential scam and seek advice on securing your accounts.
– **Monitor Your Accounts**: Keep a close watch on your financial accounts for any unauthorized transactions and report them immediately.
– **Inform Credit Bureaus**: Consider placing a fraud alert on your credit report to prevent the scammer from opening new accounts in your name.
– **Be Cautious of Future Communications**: Stay vigilant regarding any future messages from unknown sources, as scammers may attempt to target you again.
### Consider Identity Theft Protection
If your personal information has been compromised, consider enrolling in an identity theft protection service. These services can guide you through the reporting and recovery process and may offer identity theft insurance to cover losses and legal fees.
### Final Thoughts
Janet’s experience serves as a stark reminder that anyone can fall victim to well-crafted scams designed to exploit fear and urgency. By recognizing red flags such as unsolicited pop-ups, high-pressure tactics, and requests for remote access, you can better protect yourself and your personal information. Should you ever find yourself in a situation like Janet’s, remember to stay calm, verify any alerts, and take the necessary steps to secure your system. Scammers rely on impulsive reactions—take control of the situation and act thoughtfully.
Have you encountered any new scams that others should be aware of? Share your experiences with us, and let’s work together to keep our community informed.
For more tech tips and security alerts, consider subscribing to our newsletter for regular updates. Stay safe online!